How to Communicate Your Security and Compliance Posture to Build Trust With Customers
Do your customers know about your compliance efforts and trust your organization’s ability to keep their data safe? Securing customer’s data is only half the job today—corporate reputation rests on customer trust and how effectively your organization can demonstrate the ability to protect data and comply with privacy regulations.
Trust originates with transparency. Today’s technology buyers want their tech vendors to practice a full-disclosure approach to security assurance. In a recent study released by the Ponemon Institute, 73% of companies prefer to purchase from technology providers that are transparent and proactive in finding and mitigating security vulnerabilities within their own product.
Consumers also demand consistency and proof—71% of respondents said it’s highly important for technology providers to offer ongoing security assurance and evidence that components operate in a known and trusted state.
Your enterprise’s reputation and future success depends on your ability to effectively communicate your corporate security and compliance posture to customers. This article will discuss how to communicate your organization’s security and compliance stance in a way that builds trust with current and future customers.
The key steps for building trust
Why do your customers choose to buy from you? Most likely, you earned their trust by demonstrating desirable characteristics. Today, security has become a highly desirable characteristic, right next to product quality and performance, with significant influence on purchase decisions. Customers want to buy from companies that prioritize security. How do you show customers that they don’t need to worry about your security posture? According to Ponemon Institute’s research, here are the behaviors that will earn you points:
Transparency: The more transparent a provider can be about security updates and available mitigations, the better they will cement customer trust and strengthen the partnership.
Vulnerability control: Technology customers want to buy from vendors who proactively identify and correct their product vulnerabilities before customers know about them.
Evidence-backed consistency: Buyers want to see their vendors consistently providing evidence that their system’s components are operating in a known and trusted state.
How can your organization demonstrate these valued characteristics and begin earning customer trust?
It all starts with communication, and simply saying, “Hey, we’re secure” isn’t enough today. Customers need to know how risk is being reduced, and security assurance requires organizations to reveal the procedures, processes, and controls they’ve put in place to ensure data security and compliance. Here are the critical action steps to help build customer trust in your organization’s security and compliance posture:
1. Communicate how you safeguard data
Start building trust by giving customers more transparency into the processes, procedures, and controls used to protect the data that’s processed within your product and through all customer interactions. Security should be built into every infrastructure layer with proof of replication, backup, and a disaster recovery plan. Intelligent enterprises show how their networks lock down data with encryption and advanced threat protection. Talk about your identity, authentication, and user permission controls if they are robust. Be prepared to reveal to customers which vendors are within your supply chain and your processes and protocols for vetting vendors from a security and privacy standpoint.

What have you done to ensure sufficient product security? Customers will want to see how your organization demonstrates a culture of security prioritization, starting with vigorous product testing throughout the entire software development lifecycle.
Is your organization working with independent security researchers, allowing them to test for and report on any potential security vulnerabilities? If so, be sure to inform your customers, as third-party testing boosts credibility.
2. Communicate the product user’s role in security
Ideally, data security is a team sport, best addressed in a partner relationship. Christian Espinosa, the founder of Alpine Security and author of “The Smartest Person in the Room,” explains, “Transparency tends to fall apart when we view security through the lens of a vendor-client relationship rather than a partnership. In a true transparent partnership, customers are in the know so they can do their part to improve security.”
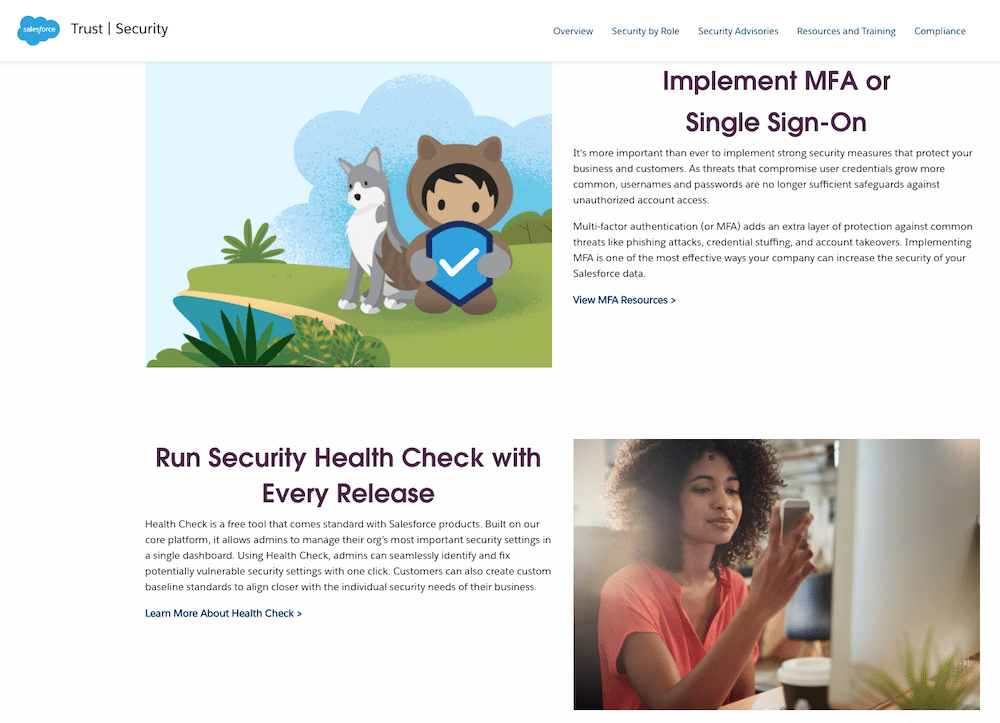
SalesForce provides an excellent example of this shared responsibility mindset. This company publishes detailed information on how they’re protecting data and provides resources for Salesforce administrators and developers on security practices. SalesForce also publishes a customer best-practice suggestion list to provide guidance on data security. Best-practice suggestions for Salesforce customers include the use of multi-factor authentication (MFA), setting safe IP login ranges, decreasing session timeout thresholds, and requiring the use of Transport Layer Security (TLS) 1.2 or higher. SalesForce also recommends their customers use Healthcheck, a holistic management tool that identifies and mitigates vulnerabilities from a single dashboard.
3. Promptly notify customers in the event of a compromise
Transparency is most critical in the event of a compromise, as this is when customers demand nothing less than fast and accurate information. To maintain customer trust after a compromise, taking immediate ownership while providing solutions to your customers is the only viable option. Christian Espinosa explains, “Customers would always rather know sooner rather than later. Too many organizations try to sweep events under the rug and hope they go unnoticed. When customers do lift up the rug and realize you knew about the issue for months, they get angry, and trust is broken.”
Do you know how to build a solid cybersecurity incident response plan?
4. Proactively update customers on vulnerability investigation
Proactively updating your customers on all testing and vulnerability investigation results is an important step in delivering transparency and boosting trust.
When vulnerabilities appear, does your team conduct investigations? Are the investigation results made readily available for public consumption? Many companies like SalesForce use public Security Advisories to keep customers current on security topics. These public databases post critical information on software security issues, complete with newly discovered events, explanations, fixes, and patch updates. Microsoft has a Security Response Center to provide customers with easily accessible vulnerability advisories. Apache also provides a comprehensive advisory database of identified issues with current fixes and updates.

5. Assist customers with meeting their own compliance obligations
Many organizations find themselves challenged to comply with a growing number of data privacy regulations and industry standards. Helping your customers with compliance goes a long way today—the more you can educate and assist your customers in achieving their compliance obligations, the more they will trust you. Are you providing resources to help your customers better understand and comply with data privacy laws? Are you clearly communicating how your product can simplify compliance for your customers?
Salesforce provides an excellent example of compliance assistance by publishing a resource list designed to help companies comply with GDPR requirements. This resource recommends important security measures like data segregation, encryption, pseudonymization, anonymization, and the use of a data controller to oversee the implementation of these practices.
Some companies like Amazon Web Services (AWS) take compliance assistance a step further by providing their customers access to a portal where AWS compliance reports are available. AWS makes it easy for customers and prospects to understand the certifications, regulations, and frameworks AWS aligns with to support customer compliance.
6. Publish your certifications, standards, and regulations
Customer trust can be furthered by providing a comprehensive set of applicable compliance certifications your organization has achieved, and the standards and regulations you adhere to. SalesForce demonstrates this best practice by providing a comprehensive compliance resource that lists 33 certifications, standards, and regulations they’ve achieved, including GDPR, FedRAMP, HIPAA, PCI DSS, and ISO 27001.
Want to see how Hyperproof can help you achieve IT security certifications, standards, and regulations?

7. Provide a forum to facilitate transparency and collaboration
Customers want security assurance from a vendor, but they also need a forum to raise their security concerns. Do you provide your customers a line of communication where they can easily report security or compliance issues?
For organizations looking to build trust through transparency, maintaining a public-facing website is essential. Websites offer the opportunity for full disclosure about your system status, security posture, and compliance. This type of transparency fuels customer trust, but unfortunately, many enterprises today aren’t maximizing this opportunity. Christian Espinosa explains, “Many companies put sales logos on their website, but don’t really tell you where they are in terms of customer risk exposure and what they’re doing to reduce it. From a transparency perspective, organizations need to say ‘here’s what your risk will be working with us and here’s what we are doing to minimize it as much as possible in the future.’”
Okta provides an example of a successful public-facing website where customers have access to the Okta Trust Page which serves as a hub for real-time information on performance, security, and compliance. Forgerock is another leader with an exemplary website emphasizing “security as a company value” and providing details of how the company incorporates security into personnel, development, and testing. Forgerock’s website also lists all external certifications held as further evidence of the company’s commitment to security and compliance.

Hyperproof facilitates effective communication regarding your security and compliance practices
If you’re selling a technology product, providing transparency around your security practices—showing customers evidence of a security-centric culture and updated proof of functioning security safeguards — has become a key element to earning and maintaining customer trust. This can be quite a challenge when companies don’t have an organized system for collecting and managing proof of their security and compliance activities.
Hyperproof’s compliance operations platform can help you add more rigor to your security and IT compliance programs and help you demonstrate your compliance position more easily. With Hyperproof, you can:
- Track all risks, compliance requirements, controls (i.e., documentations of your security and data privacy safeguards) and evidence of internal and vendor compliance activities in a single platform
- Align your security and compliance activities to industry standards (e.g., ISO 27001, NIST CSF) and regulatory requirements (e.g., GDPR)
- Easily gather and manage proof of proper security controls and system function for audits
- Automate workflows and reminders around evidence collection and controls evaluations
As Carl Lombardi, VP of Operations at Prime8 explains, “With Hyperproof as the system of record for all of my work, I am ready for a regulator or customer to come in and do a spot audit at any time. I would feel comfortable showing an auditor what the company is doing, because the evidence is in the tool.”
Maintaining security and compliance is an ongoing challenge, but by partnering with Hyperproof, your organization will be well equipped to demonstrate a transparent and trustworthy security posture in the eyes of your customers.
To see how Hyperproof can help you maintain a consistent, efficient, and effective security compliance program, sign up for a demo.
See Hyperproof in Action
Related Resources
Ready to see
Hyperproof in action?